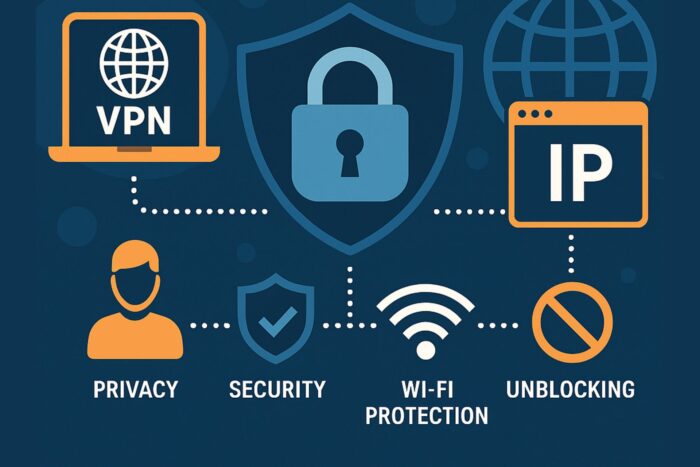
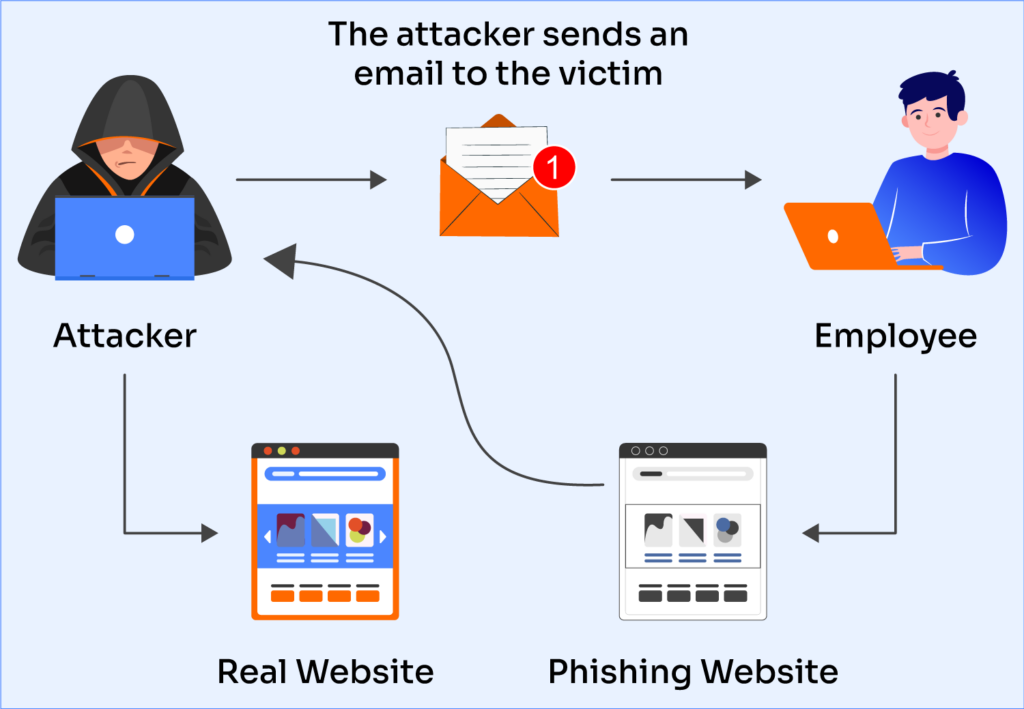
10 Essential Cybersecurity Tips to Protect Your Online Privacy
In today’s digital landscape, our lives are intertwined with technology like never before. We share personal information, engage in online shopping, and connect with others at the click of a button. While this convenience is fantastic, it also comes with risks that can compromise our cybersecurity and privacy. With cyber threats lurking around every corner, … Read more